Cloud-Enabled vs. Cloud-Native Access Control Systems.
- GK Tieo
- Jan 21
- 4 min read

Architectural Differences, Strategic Implications, and Long-Term Risk
Executive Summary
The access control industry is undergoing a structural shift driven by cloud computing, digital identity, and increasing cybersecurity and compliance pressures. While many solutions are now marketed as “cloud-based,” significant architectural differences exist beneath similar terminology.
Two terms—cloud-enabled and cloud-native—are frequently used interchangeably, despite representing fundamentally different system designs. These differences directly affect security resilience, scalability, operational cost, compliance readiness, and long-term viability.
This white paper provides a clear, technical, and strategic comparison between cloud-enabled and cloud-native access control systems. It outlines architectural distinctions, operational consequences, and future trends to support informed decision-making for enterprise buyers, consultants, and system integrators.
1. Background: The Evolution of Access Control Architecture
Traditional access control systems were designed around localized infrastructure. Controllers, databases, and decision logic resided on-site, reflecting an era where connectivity was unreliable and centralized computing impractical.
As organizations expanded geographically and operational complexity increased, limitations emerged:
Fragmented identity management
Manual system updates
High operational overhead
Limited integration capabilities
The adoption of cloud computing promised to address these issues. However, the industry responded in two distinct ways:
Extending legacy systems to connect to the cloud
Rebuilding systems specifically for cloud environments
These approaches produced what are now known as cloud-enabled and cloud-native systems.
2. Defining Cloud-Enabled Access Control
A cloud-enabled access control system originates from a legacy on-premise design that has been enhanced with cloud connectivity.
2.1 Core Characteristics
Local server or appliance remains the system of record
Controllers make access decisions independently
Cloud services provide:
Remote visibility
Event monitoring
Data backup
Web-based management interfaces
Software updates are periodic and often site-specific
Offline operation is assumed as the default state
2.2 Architectural Implications
The cloud functions as a supervisory layer rather than a control plane. Each site operates semi-independently, requiring synchronization mechanisms to maintain consistency.
This architecture reflects incremental modernization rather than fundamental redesign.
3. Defining Cloud-Native Access Control
A cloud-native access control system is designed from inception to operate within cloud infrastructure.
3.1 Core Characteristics
Cloud platform serves as the system of record
Identity, policy, credentials, and audit data are centrally managed
Edge devices act as secure execution points
Built using modern cloud principles:
Microservices
API-first design
Continuous deployment
Elastic scalability
Centralized monitoring, patching, and governance
3.2 Architectural Implications
Decision logic and policy management are centralized, while resilience is achieved through intelligent edge caching and failover mechanisms.
This model treats access control as a distributed service rather than a collection of isolated systems.
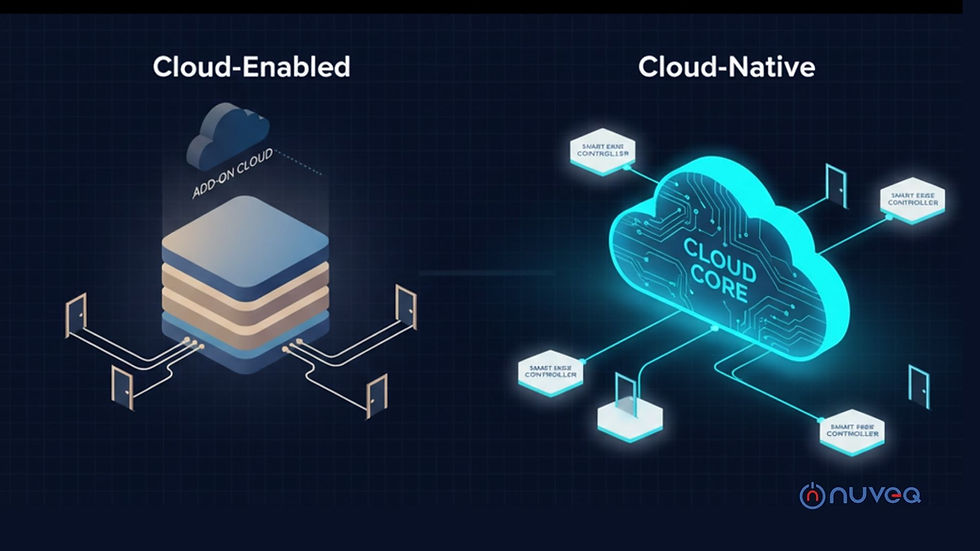
4. Architectural Comparison
4.1 System of Record
Cloud-enabled: Local database at each site
Cloud-native: Centralized cloud identity and policy store
4.2 Decision Authority
Cloud-enabled: Local controllers validate credentials
Cloud-native: Central policy engine governs access, executed at the edge
4.3 Scalability Model
Cloud-enabled: Linear scaling with added infrastructure
Cloud-native: Elastic scaling without architectural change
4.4 Integration Capability
Cloud-enabled: Limited, often via middleware
Cloud-native: Native API-based ecosystem integration
5. Security and Cyber Risk Considerations
5.1 Patch Management
Legacy-derived systems typically rely on manual or scheduled updates, increasing vulnerability windows.
Cloud-native systems support:
Continuous security patching
Centralized vulnerability mitigation
Consistent version control across all sites
5.2 Identity-Centric Security
Modern access control increasingly aligns with enterprise identity strategies, including:
Mobile credentials
Workforce lifecycle automation
Zero-trust frameworks
Cloud-native platforms integrate naturally with identity providers, while cloud-enabled systems often require synchronization layers that introduce complexity and risk.
6. Operational Impact Over the System Lifecycle
6.1 Total Cost of Ownership
Initial deployment costs may favor cloud-enabled solutions due to hardware reuse. However, over time:
Local servers require maintenance and replacement
Backup and disaster recovery strategies multiply
Site-by-site troubleshooting increases
Cloud-native platforms reduce infrastructure footprint and centralize operations, resulting in lower long-term operational overhead for multi-site deployments.
6.2 Day-2 and Day-500 Operations
Operational efficiency depends less on installation and more on ongoing management:
User provisioning
Policy updates
Compliance audits
Incident response
Cloud-native architectures are optimized for these continuous activities.
7. Reliability and Connectivity Resilience
A common concern regarding cloud-native systems is dependency on internet connectivity. Modern cloud-native designs address this through:
Credential and policy caching at the edge
Deterministic fail-secure and fail-safe behaviors
Event synchronization upon reconnection
Cloud-enabled systems may experience inconsistent states during partial outages due to asynchronous synchronization models.
8. Integration and Ecosystem Readiness
Access control increasingly functions as part of a broader digital ecosystem, interacting with:
HR systems
Building management systems
Visitor management platforms
Security operations centers
Cloud-native platforms are inherently designed for real-time, event-driven integration through standardized APIs, enabling automation and data-driven security operations.
9. Industry Outlook: Strategic Predictions
9.1 Cloud-Enabled as a Transitional Architecture
Cloud-enabled systems will remain relevant in retrofit and legacy environments but will increasingly be viewed as interim solutions rather than long-term platforms.
9.2 Identity-Driven Access Control Will Dominate
As physical and digital identity converge, centralized identity platforms will favor cloud-native access control architectures.
9.3 Compliance and Cybersecurity Will Drive Adoption
Regulatory scrutiny, cyber insurance requirements, and board-level risk oversight will accelerate adoption of architectures that support centralized governance and auditability.
10. Decision Framework for Buyers and Consultants
Organizations evaluating access control platforms should assess:
Where does authoritative identity data reside?
How are policies enforced and updated?
How is cybersecurity managed across the system lifecycle?
What is required to scale from one site to fifty?
How does the platform integrate with future identity and security systems?
The answers to these questions typically reveal whether a system is cloud-enabled or cloud-native.
Conclusion
The distinction between cloud-enabled and cloud-native access control systems is architectural, not semantic.
While both leverage cloud technologies, only cloud-native systems are fundamentally designed to meet the operational, security, and scalability demands of modern enterprises.
In access control, architecture determines long-term risk, cost, and adaptability. Organizations that understand and evaluate this distinction are better positioned to build resilient, future-ready security infrastructures.








Comments